Vulnerability management
runZero imports vulnerability reports from leading endpoint management and vulnerability management platforms.
In addition to importing data, runZero natively reports vulnerability information in the following categories:
-
Applications that expose data without authentication
-
Actively exploited vulnerabilities in the wild
-
Devices and applications using default logins
-
End-of-Life hardware, firmware, and software
-
Shared and compromised encryption keys
-
Expired and insecure certificates
-
Devices from embargoed manufacturers
-
Internet exposure of management services
-
Internet exposure of internal assets
-
Internet exposure of operational technology
-
Insecure protocol configurations
-
Missing security controls
-
Network outliers
runZero & Nuclei
In addition to native capabilities, runZero scans can also make use of the Nuclei open source vulnerability scanner. A modified version of the Nuclei engine is embedded into the runZero Explorer and CLI binaries. These binaries also include a set of curated vulnerability checks (templates) that can be selected from the runZero scan configuration. runZero’s Nuclei templates are open source and regularly submitted back to the upstream project.
Early access
Use of Nuclei within runZero is still early access and not enabled by default.
To enable Nuclei templates within a runZero scan:
-
Ensure that you are using runZero 4.0.250606.0 or newer
-
Create or modify a new Scan Task
-
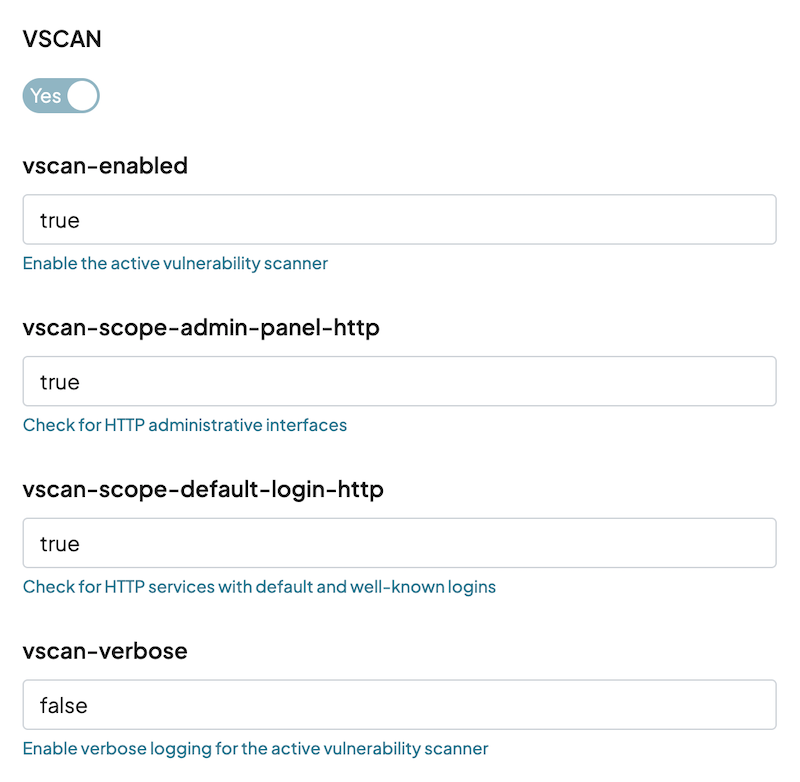
Under the Probes & SNMP tab, search for the vscan probe.
-
Set the vscan-enabled, vscan-scope-admin-panel-http, and vscan-scope-default-login-http values to true.
-
Save and/or launch the scan task.
These settings enable detections for exposed web panels and default and weak credentials within web interfaces.
Approximately 240 templates are enabled today. These templates only run when runZero’s precise fingerprinting determines that the specific asset and service is appropriate for the template. As a result, including these options generally does not noticeably increase the amount of time that a scan takes.
There are a couple caveats:
-
Default login tests, even for HTTP interfaces, can result in account lockouts. The default settings of things like Apache Tomcat and CrushFTP can result in the administrative accounts being temporarily locked as the result of a scan.
-
Templates may not run if there is a gap in runZero’s fingerprinting or the service presents a variant that we haven’t seen before. Our goal is to be as safe as possible and this is one of the tradeoffs compared to running Nuclei as a standalone tool.
If you’d like to see extensive logs for what decisions are made by the scan engine, set the vscan-verbose option to true and review the task logs after the scan completes.
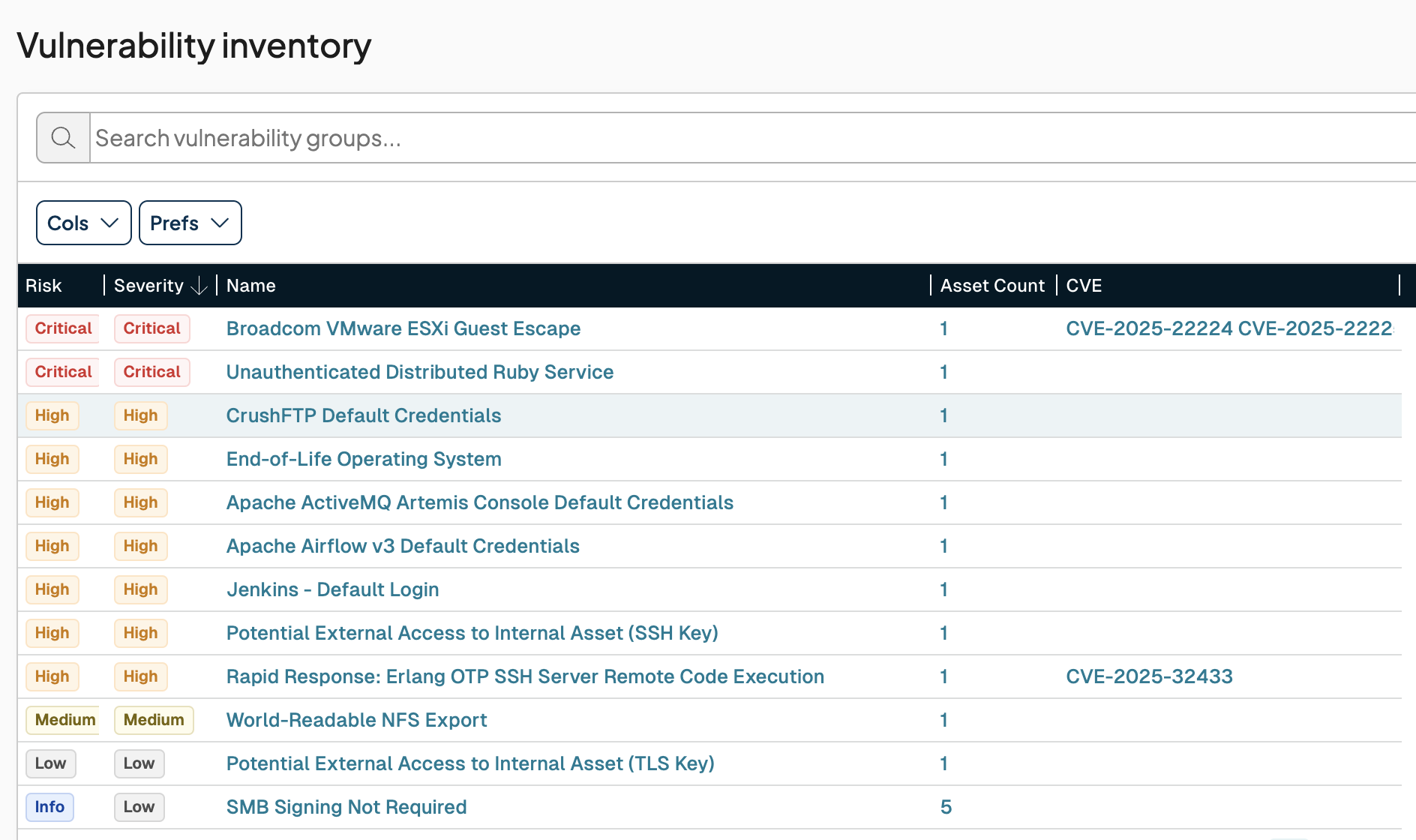
After the scan completes, any identified vulnerabilities and findings will be shown in the respective product sections.
Future plans
runZero plans to support a wide assortment of new coverage through the Nuclei engine.
Our near-term plans include:
-
Dedicated configuration elements for vulnerability check selection
-
Extending default-login templates to cover non-HTTP protocols (SSH, Telnet, FTP)
-
Rapid Response templates for emerging vulnerabilities
-
Extended coverage of important vulnerabilities
Slightly longer-term, we would like to support customer-provided templates and template libraries.
From an open-source perspective, we have a ton of ideas for improving the Nuclei engine, including linking Nuclei with SSHamble and excrypto.